Overview
XPTester is short for XACML Policy Tester and is a scalable, efficient and effective tool for XACML policy testing. Using XPTester, the policy tester only push one button to obtain a comprehensive testing report that aids him in locating errors in the policy(if there is any). XPTester is designed and developed by Software Engineering Group, Nanjing University.
XPTester is
- Scalable
- Efficient
- Effective
XPTester is capable of dealing with XACML policy containing tens to thousands of rules, notably, at a very low cost of time and space.
Even for XACML policy containing thousands of rules, it only takes XPTester about 30 to 40 seconds in generating a testing report. For small policies, say, containing only several rules, the period is even shorter, within 10 seconds on overall.
XPTester fully takes consideration of different Combining Algorithms(current version of XPTester supports First-Applicable, Permit-Overrides, Deny-Overrides and Only-One-Applicable) and Functions(in current prototype only a small part of them is supported for demo purpose) in XACML. Moreover, XPTester generates test requests based on KLEE, which is known as the best symbolic execution tool till now, thus supplying the policy under test with adequate test requests to cover it all around. So XPTester is effective in disclosing errors in policy.
Approach and Implementation
In XPTester, First, XACML policy under test is converted into semantically equivalent C Code Representation(CCR). Second, the CCR are symbolically executed by exploring all the touchable branches to generate test inputs. Final, the test inputs are used to compose access control requests which can be automatically evaluated by existing policy evaluators against the XACML policies to report the defects.
Following is the system architecture of XPTester:
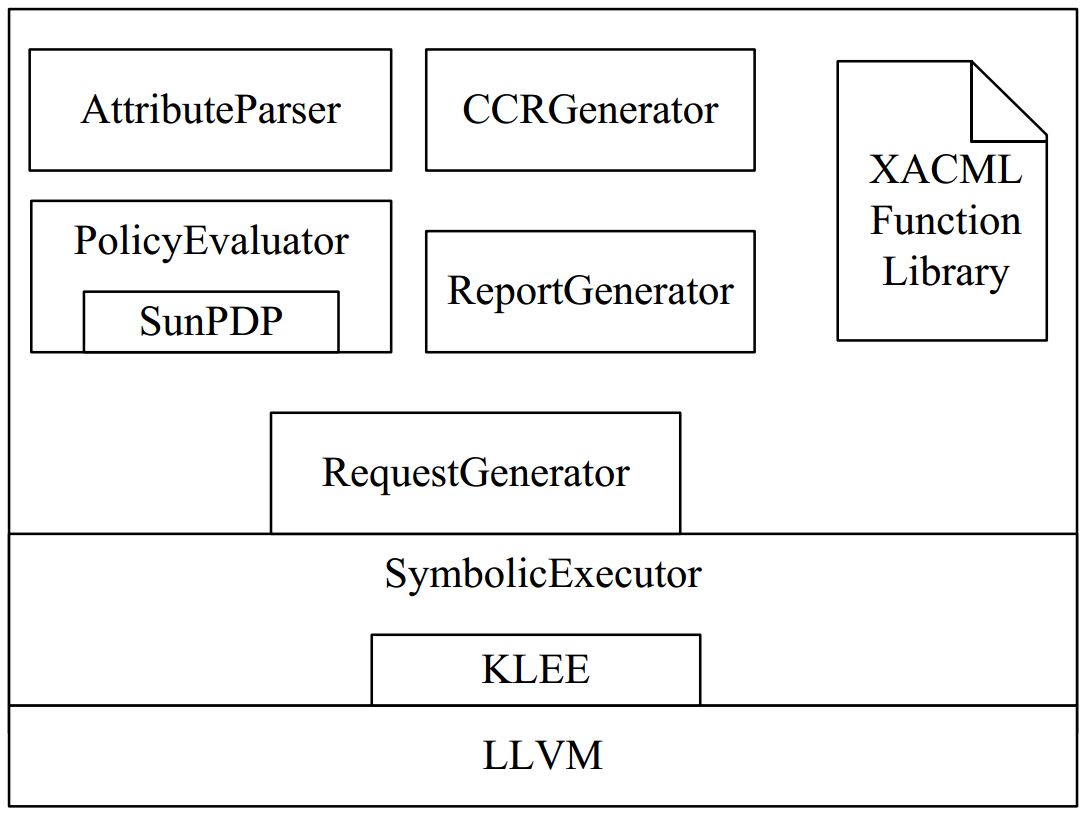
It has a three-tier architecture. At the bottom layer is the LLVM compiler infrastrcuture. The CCR is compiled into LLVM bitcode and running on LLVM with KLEE as the execution engine. Upon the LLVM layer is SymbolicExecutor, which encapsulates KLEE. It feeds LLVM bitcode file into KLEE and invokes KLEE to obtain test inputs for CCR. The top-most level contains several components including AttributeParser which implements attribute numeralization, CCRGenerator which converts XACML policy into CCR, RequestGenerator which composes XACML requests based on the test inputs generated by SymbolicExecutor, PolicyEvaluator which is based on SunPDP and acts as policy evaluation engine to get decisions to access requests, and ReportGenerator which generates testing reports. There are hundreds of Functions defined in XACML to enhance the restriction on the type of request to which the policy can be applied. We build a library which defines c functions representing Functions in XACML.
You may refer to the Running Example to take an insight look at how XPTester works.
Download and Installation
You may download the latest version of XPTester from here.
Last updated: 1/23/2014.